Adobe Connect Directory Service Integration for LDAP Sync and Authentication – Explained
The following article is intended to show how the directory service integration works with the current release of Adobe Connect 9.1 and how it relates to setting up a synchronization. I will follow this article up with another regarding Authentication. For the most part, this is applicable for any flavor of Adobe Connect 8 or 9.
Adobe Connect lets on-premise (licensed) customers integrate their own company’s LDAP directories with the Adobe Connect database and synchronize users and groups from their directory into Adobe Connect for easy user account management. Any LDAP v.3 directory server may integrate with Adobe Connect, however the following are directory servers that have been officially tested by Adobe to work with Connect:
- Active Directory Application Mode (ADAM) with Service Pack 1 for Windows Server 2003
- Active Directory (Windows Server 2003) Windows Server 2003 and later
- Active Directory (Windows 2000 Server)
- IBM Tivoli Directory Server 6.1
- Novell eDirectory 8.8
- OpenLDAP 2.3.35
- Sun™ Java™ System Directory Server 5.2
This list isn’t all directories that will work with Adobe Connect. It is again, just directories that have been tested and certified to work with Connect.
The directory I am using for this tutorial is a free lightweight LDAP directory called ‘OpenDJ‘ that runs on Java.
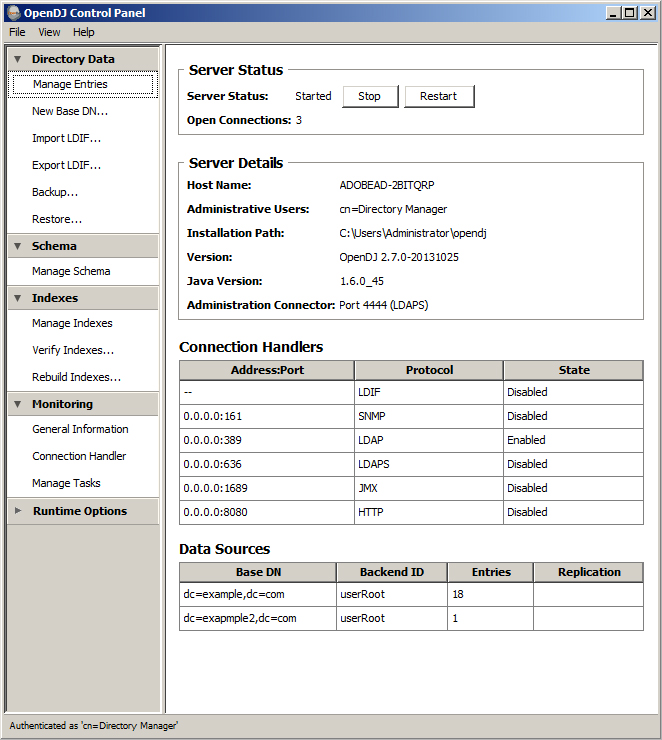
Below is a screenshot of my general settings in OpenDJ.
My LDAP host happens to be my machine name. This will obviously be different in your directory.
My Admin Username is the default (cn=Directory Manager). This will obviously be different in your directory.
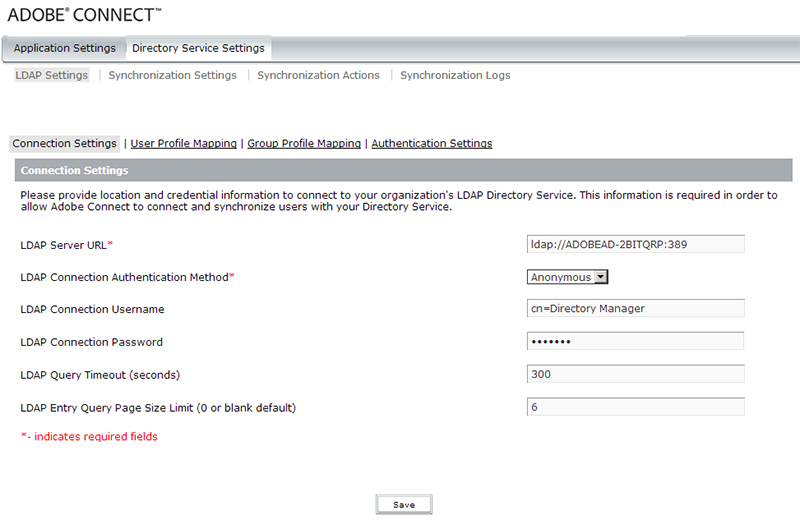
To setup the initial Connection Settings for Adobe Connect LDAP integration in Adobe Connect’s administration console (http://localhost:8510/console), you will navigate to Directory Service Settings (as shown below):
The LDAP Server URL will be the LDAP host value you are connecting to. You will include the protocol (ldap://) and the port (:389). The above is my example. Your directory will be different and the port/protocol may be different.
The LDAP Connection Authentication Method will be a selection of either Anonymous, Simple, or Digest MD5. It will depend on your directory.
The LDAP Connection Username is the binding agent username you are using to connect to the directory. You need Read access to the directory. The above example is my example for my directory. Your will be different.
The LDAP Connection Password is the binding agent’s password you are using to connect to the directory with.
The LDAP Query Timeout (seconds) value is the amount of seconds you will wait until the query times out (if no response).
The LDAP Entry Query Page Size Limit (0 or blank default) is the page size value for the directory. Directories tend to have a page size limit (AD specifically) of 1000 records. So if you have have many thousands of records you want to bring in, you need to have that many pages per 1000 records you anticipate to bring in. Ex. 5 if 5000 records. 10 if 10,000 records, etc.
When you click the ‘Save’ button, if all the settings are correct and Adobe Connect can successfully connect to and authenticate with the LDAP directory, you will get the below message in red, indicating that the settings were saved and connectivity has been verified.
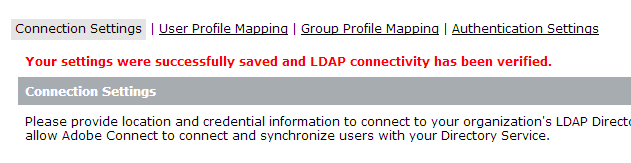
{localhost: 8510/console} > Directory Service Settings > LDAP Settings > Connection Settings > {post save page}
Let’s say if I mistakenly typed in the wrong LDAP Host (added an ‘s’ at the end by mistake), you will get the following below if the connectivity can not be verified.
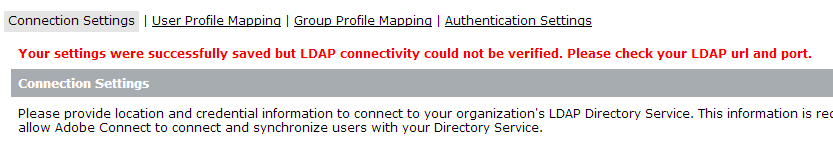
{localhost: 8510/console} > Directory Service Settings > LDAP Settings > Connection Settings > {post save page}
If you can’t figure out what you are doing incorrect, the Adobe Connect debug.log will show you the attempt at connecting and will point out the following error if the host value (as an example) is incorrect.
[01-14 14:10:42,125] console-8510-11 (INFO) LDAPConfigReader: LDAP authentication is enabled with following settings:
[01-14 14:10:42,125] console-8510-11 (INFO) LDAPConfigReader: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings:
AdminUsername: cn=Directory Manager
AdminPassword: (hidden)
AuthType: none
Group Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Women,dc=example,dc=com
Filter: (objectClass=groupOfNames)
isSearchRecursive: true
Group Branch 1: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Men,dc=example,dc=com
Filter: (objectClass=groupOfNames)
isSearchRecursive: true
GroupMembershipMapping: member
GroupNameMapping: cn
QueryTimeout: 300
Query Page Size: 6
Url: ldap://ADOBEAD-2BITQRPs:389
User Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Men,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 1: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Women,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
UserFirstnameMapping: givenName
UserLastnameMapping: sn
UserLoginMapping: uid
UserInfoMappings: {}
UserSyncMappings: {first-name=givenName, email=mail, x-26095=roomNumber, login=uid, last-name=sn, x-26088=initials}
DirectoryMappings: {authentication-enabled=true, fallback-enabled=true, user-account-type=internal, create-user-account=true, user-groups-on-first-login-only=false, user-groups-enrollment=null}
[01-14 14:10:42,125] console-8510-11 (INFO) LDAPLoginManager: 2ms login configuration read
[01-14 14:10:42,532] console-8510-11 (ERROR) Exception thrown
javax.naming.CommunicationException: ADOBEAD-2BITQRPs:389 [Root exception is java.net.UnknownHostException: ADOBEAD-2BITQRPs]
at com.sun.jndi.ldap.Connection.<init>(Connection.java:209)
at com.sun.jndi.ldap.LdapClient.<init>(LdapClient.java:116)
at com.sun.jndi.ldap.LdapClient.getInstance(LdapClient.java:1580)
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2678)
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:296)
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURL(LdapCtxFactory.java:175)
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURLs(LdapCtxFactory.java:193)
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxInstance(LdapCtxFactory.java:136)
at com.sun.jndi.ldap.LdapCtxFactory.getInitialContext(LdapCtxFactory.java:66)
at javax.naming.spi.NamingManager.getInitialContext(NamingManager.java:667)
at javax.naming.InitialContext.getDefaultInitCtx(InitialContext.java:288)
at javax.naming.InitialContext.init(InitialContext.java:223)
at javax.naming.InitialContext.<init>(InitialContext.java:197)
at javax.naming.directory.InitialDirContext.<init>(InitialDirContext.java:82)
at com.macromedia.breeze.ldap.auth.LDAPLoginManager$TestConnection.execute(LDAPLoginManager.java:148)
at com.macromedia.airspeed.ActionHandler.executeOrQueue(ActionHandler.java:141)
at com.macromedia.airspeed.ActionDispatcher.dispatch(ActionDispatcher.java:344)
at com.macromedia.airspeed.servlet.HTMLHandler.execute(HTMLHandler.java:544)
at com.macromedia.airspeed.servlet.HTMLHandler.service(HTMLHandler.java:209)
at com.macromedia.airspeed.servlet.BaseServlet.service(BaseServlet.java:436)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:728)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:305)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:210)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:222)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:123)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:472)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:171)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:99)
at org.apache.catalina.valves.AccessLogValve.invoke(AccessLogValve.java:936)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:118)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:407)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:1004)
at org.apache.coyote.AbstractProtocol$AbstractConnectionHandler.process(AbstractProtocol.java:589)
at org.apache.tomcat.util.net.JIoEndpoint$SocketProcessor.run(JIoEndpoint.java:310)
at java.util.concurrent.ThreadPoolExecutor$Worker.runTask(ThreadPoolExecutor.java:886)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:908)
at java.lang.Thread.run(Thread.java:662)
Caused by: java.net.UnknownHostException: ADOBEAD-2BITQRPs
at java.net.PlainSocketImpl.connect(PlainSocketImpl.java:195)
at java.net.SocksSocketImpl.connect(SocksSocketImpl.java:366)
at java.net.Socket.connect(Socket.java:529)
at java.net.Socket.connect(Socket.java:478)
at java.net.Socket.<init>(Socket.java:375)
at java.net.Socket.<init>(Socket.java:189)
at com.sun.jndi.ldap.Connection.createSocket(Connection.java:351)
at com.sun.jndi.ldap.Connection.<init>(Connection.java:186)
… 36 more
Once you have successfully connected to your LDAP directory, you can move on to the User and Group Profile mappings. This is where we tell Adobe Connect where in the directory to look for users and groups, and what attributes to look for and pull values from.
My directory is setup so that the applicable LDAP fields for normal user creation are: sn, givenName, cn, and email. This is just my directory for the sake of this article. Your directory will most likely be different. Remember, passwords for LDAP users are not stored in Adobe Connect, so we do not map to the password field when doing an LDAP sync.
I have two different OUs created in my directory for this tutorial. One called ‘Men’ and one called ‘Women’ to make it easy to follow. Of course no directory would probably be setup this way in real life, but for the sake of this example, I’ve setup the OUs in this fashion, with some groups under each. The groups are ‘Male Learners’, ‘Female Learners’, and ‘Female Learners 2’.
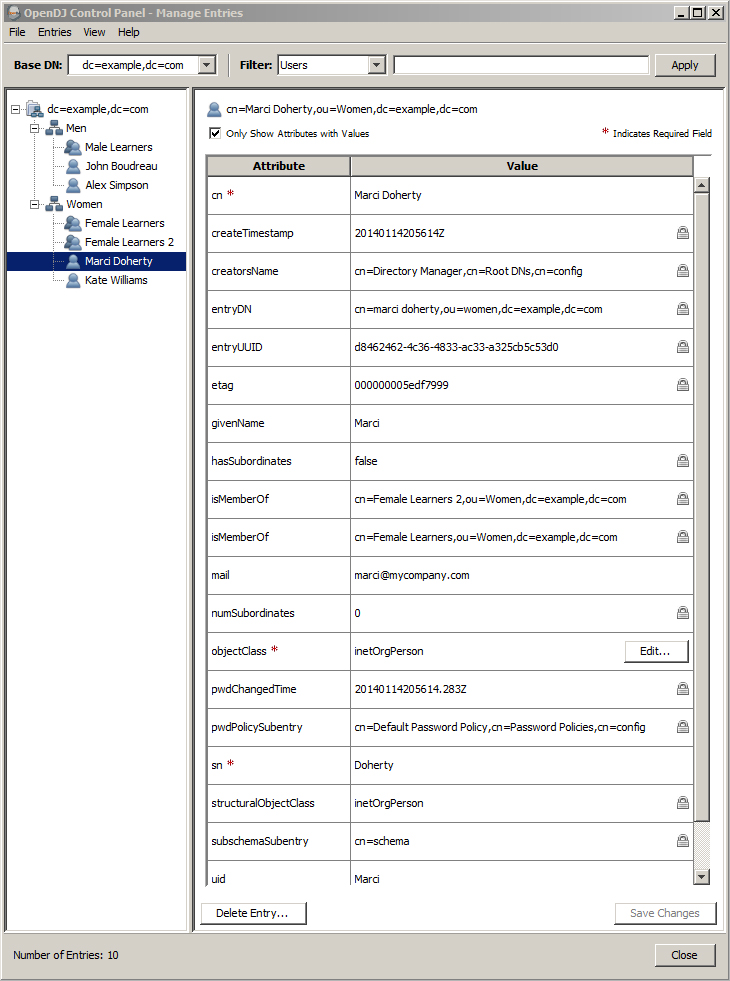
Below is a screenshot of what a user profile looks like in my directory. In this example, user Marci is selected with the following parameters:
givenName = Marci (this is the user’s first name)
sn = Doherty (this is the user’s last name)
cn = Marci Doherty (this is the full name of the user – first + last)
mail = marci@mycompany.com (this is the user’s email address)
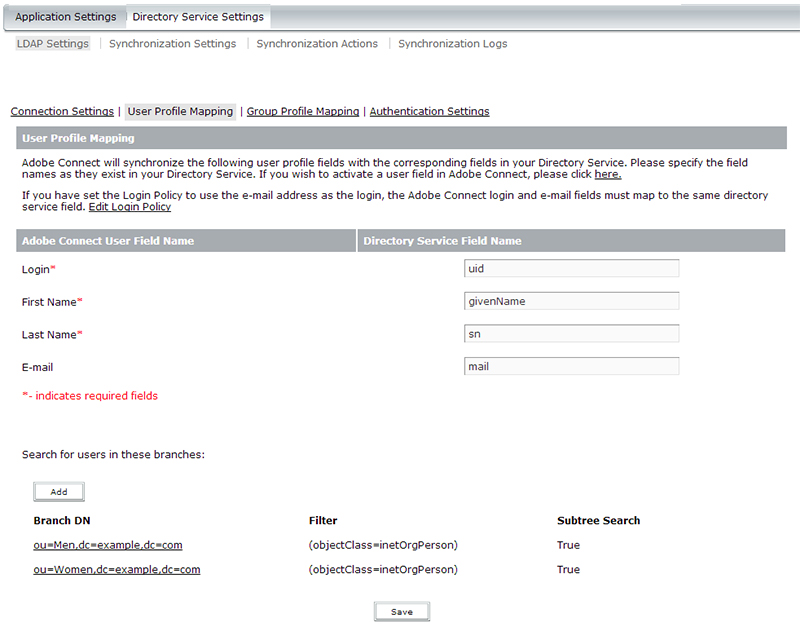
Switching back over to the Connect configuration console, we click on ‘User Profile Mappings‘ (as shown below) to get into area where we will map the Adobe Connect user profile fields to your Directory user profile fields.
The first part of the User Profile Mapping is to map the Adobe user fields with the LDAP user fields. In my above example, my Adobe Connect user profile fields are ‘Login‘, ‘First Name‘, ‘Last Name‘, and ‘E-mail‘. In the LDAP directory (as shown previously), my Login field in LDAP is actually ‘uid‘. My First Name field in LDAP is ‘givenName‘. My Last Name field in LDAP is ‘sn‘. My E-Mail field in LDAP is ‘mail‘. Essentially what you are doing is mapping the fields between both systems with one another so that Adobe Connect knows what to look for and where to put the applicable values.
The second part of the User Profile Mapping is to select the Branch DN (Distinguished Name) or Branches you are going to be looking for users in. These are basically the OUs (as in my example above) where you will be looking for users. Any user you are pulling into Adobe Connect as part of the LDAP sync, needs to reside in one of these Branches that you add. In my example above (and as indicated previously in the screenshot of my directory above), I have 2 different OUs I’ve created in my directory. One for Men and one for Women. The format for my Branches are indicated in the screenshot. ou=Men,dc=example,dc=com and ou=Women,dc=example,dc=com. The last part of the configuration for User Profile Mappings is to set a filter. This filter further tells Adobe Connect what to look for in the specified branches. For the example above, I want to only pull in ‘users’ from those OUs. I do not want to pull in other things like groups, or computers/printers, etc. If there are other things in those OUs that have those attributes, you will pull everything in if you do not filter on your search. My example uses the objectClass attribute and a value of ‘inetOrgPerson‘ which is purely specific to my directory. Your directory may have another value for a users’ objectClass attribute. You may also want to filter on some other attribute or attributes. It is purely up to you and how your data is structured.
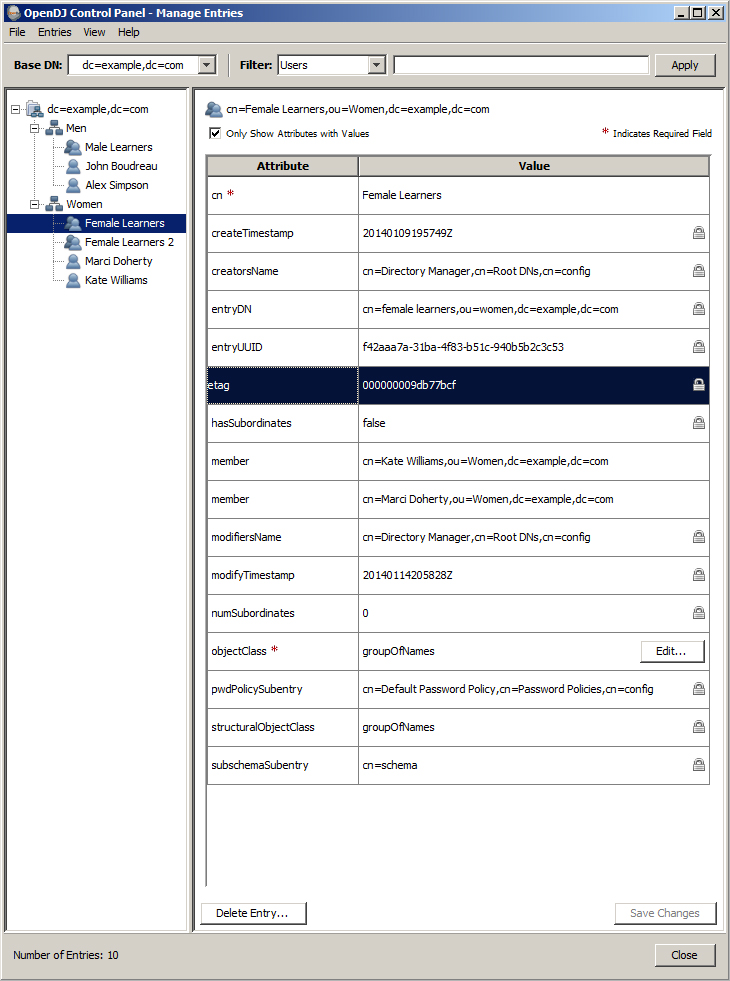
Below is a view of my directory again with a Group selected, showing the cn and member attributes. In this example, there are 2 members in this group called ‘Female Learners’. You can see both next to the ‘member’ attribute. One line for each user.
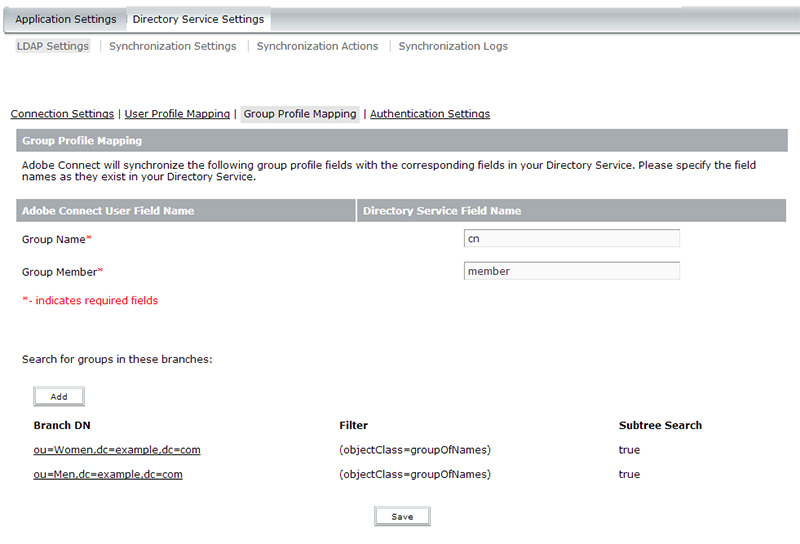
If you desire to also synchronize LDAP Groups with Adobe Connect (not required) you can click on ‘Group Profile Mappings‘ (as shown below) to get into area where we will map the Adobe Connect user profile fields to your Directory user profile fields.
In my example, my Adobe Connect group profile fields are ‘Group Name‘, and ‘Group Member. In the LDAP directory (as shown previously), my Group Name field in LDAP is ‘cn‘. My Group Member field in LDAP is ‘member‘. Again, essentially what you are doing is mapping the fields between both systems with one another so that Adobe Connect knows what to look for and where to put the applicable values.
As with the User Profile Mappings, the second part of the Group Profile Mapping is to select the Branch DN (Distinguished Name) or Branches you are going to be looking for groups. These are basically the OUs (as in my example above) where you will be looking for groups. Any group you are pulling into Adobe Connect as part of the LDAP sync, needs to reside in one of these Branches that you add. In my example above (and as indicated previously in the screenshot of my directory above), I have 2 different OUs I’ve created in my directory. One for Men and one for Women. The format for my Branches are indicated in the screenshot. ou=Men,dc=example,dc=com and ou=Women,dc=example,dc=com, just as in the User mappings. The last part of the configuration for Group Profile Mappings is to set a filter. This filter further tells Adobe Connect what to look for in the specified branches. For the example above, I want to only pull in ‘groups’ from those OUs. I do not want to pull in other things like users, etc. If there are other things in those OUs that have those attributes, you will pull everything in if you do not filter on your search. My example uses the objectClass attribute and a value of ‘groupOfNames’ which is purely specific to my directory. Your directory may have another value for a users’ objectClass attribute. You may also want to filter on some other attribute or attributes. It is purely up to you and how your data is structured.
Once you have configured all the connection settings and user and group profile mappings correctly, the next step is to setup the synchronization schedule. In the configuration console, click on ‘Synchronization Settings‘ and then view the ‘Schedule Settings’ section (as depicted below).
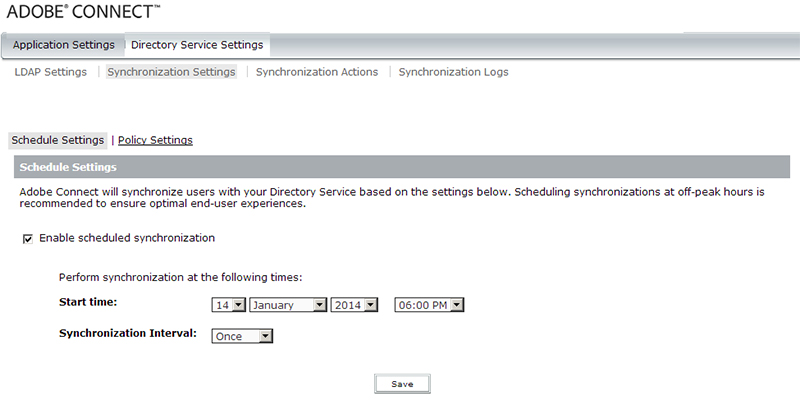
{localhost: 8510/console} > Directory Service Settings > Synchronization Settings > Schedule Settings
If you wish to schedule a synchronization, you would check the box next to ‘Enable scheduled synchronization‘ and then set a time and frequency (‘Synchronization Interval’) for the sync. The frequency you can choose from is ‘Once’, ‘Daily’, ‘Weekly’, or ‘Monthly’. If you wish to do a manual synchronization either one time only or whenever you want, without having a set scheduled sync, leave this option unchecked.
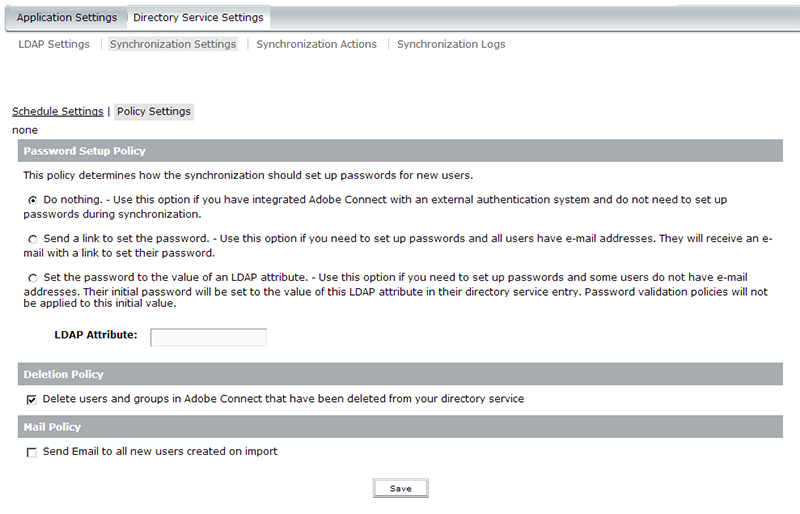
Next, you would select the ‘Policy Settings‘. The most common options on this page to use would be the Deletion Policy and the Mail Policy options. These are all optional, but the Deletion Policy would need to be checked if you want users and groups to be deleted from Adobe Connect when they are removed from LDAP. If you have this checked, and a user or group is deleted from LDAP, then on the next sync in Adobe Connect, that user or group would be removed from Adobe Connect. If you leave this option unchecked, then even if they are removed from LDAP, the users or groups would stay in Adobe Connect. The Mail Policy option would be checked if you want a New User email to go out when users are created initially with a sync.
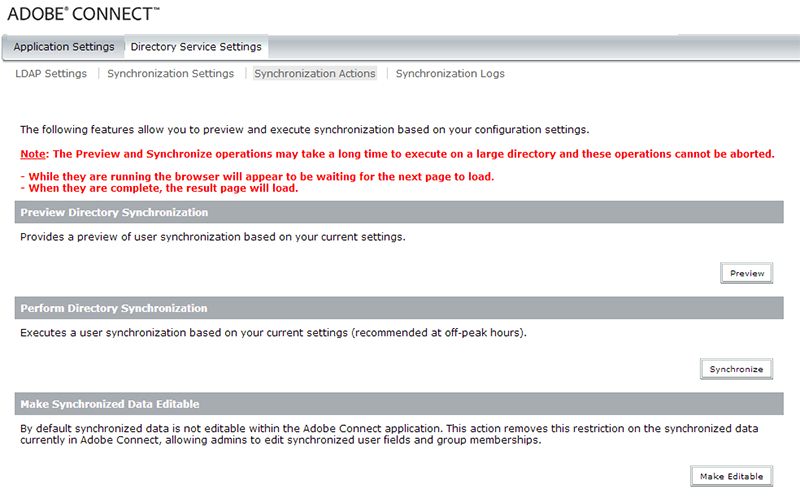
The next step would be the synchronization itself. In the configuration console, you would click on ‘Synchronization Actions‘ (as seen below). On this screen, it will allow you to Preview or Synchronize. If you ‘Preview’, it will run the synchronization in preview mode so that you can look at the log and see what exactly will happen if/when you actually run the sync. This is good to just test and see exactly what is going to happen. If you click ‘Synchronize’ it will perform the full sync with your LDAP directory.
A preview log will be generated in CSV format. You will see a screen that will show you a ‘View Results’ link. That will be the CSV you can download and open either in a text editor or MS Excel (preferred).
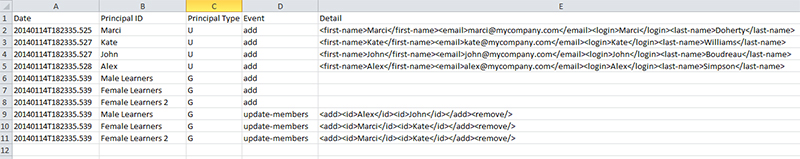
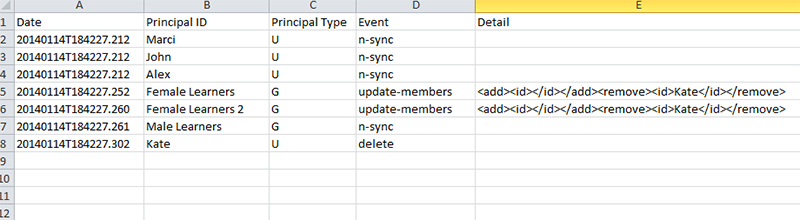
When I run my preview (again based on the directory I have shown above, and taking into consideration I have not done any sync yet), the data looks like this:
You can see from the preview.csv that all 4 of my users (Marci, Kate, John, and Alex) are all being imported. All 3 of my groups (Male Learners, Female Learners, Female Learners 2) are imported. And then users are added to groups as per the LDAP membership.
The Principal ID column shows you the object the action is being performed on.
The Principal Type column shows you ‘U’ for User or ‘G’ for Group.
The Event column will indicate the action taken. In this example, ‘add’ is the action performed for all the users and groups as obviously this is the first time they’ve ever been synchronized. You also see ‘update-members’ as an event for the group membership assignments that have also taken place.
If there are warnings or issues with the sync data, Adobe Connect will have shown you a separate csv file that is available for you to download, that will point out all the issues it found with any of the data. In this case above, there were no issues with any of the data for my users or groups.
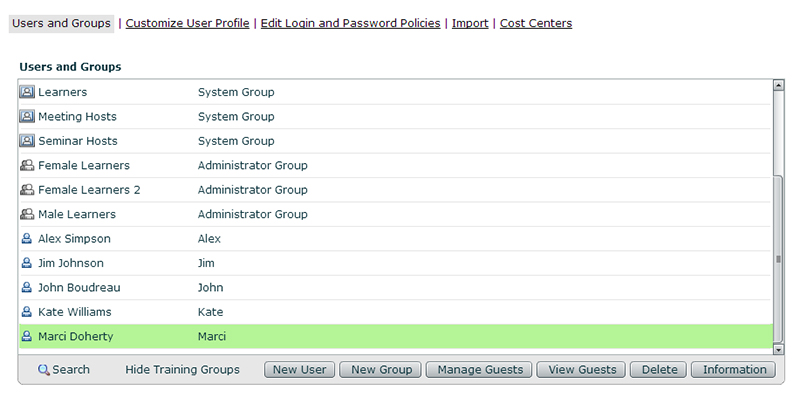
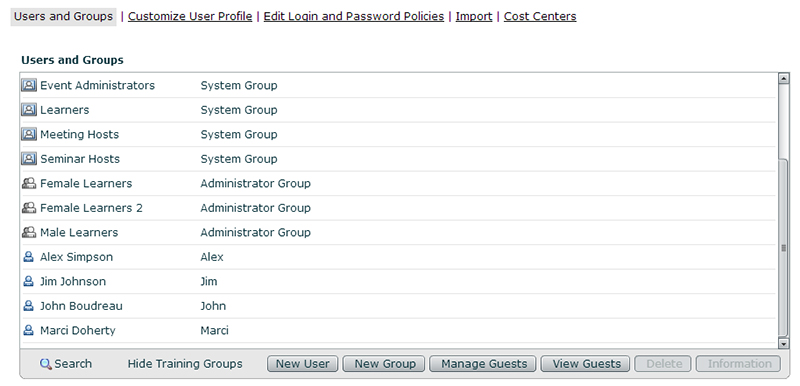
If I look in the Users and Groups section now in Adobe Connect, you will see all the users and groups that were brought in with the sync:
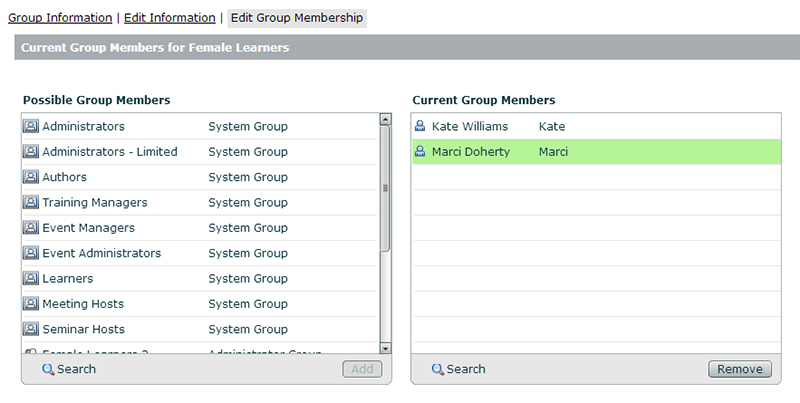
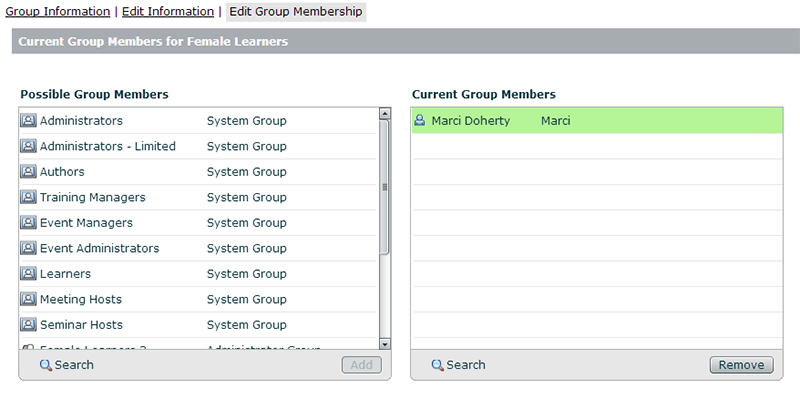
You will also see that the groups (in the example shown below, the Female Learners group) have also had the user membership populated:
For the sake of showing all the Events (and scenarios), I ran the synch once (initially above). Then I ran it again, without changing anything from the LDAP side for any of the information. So basically the synch should have done nothing new. You can see this by looking at the new sync log:
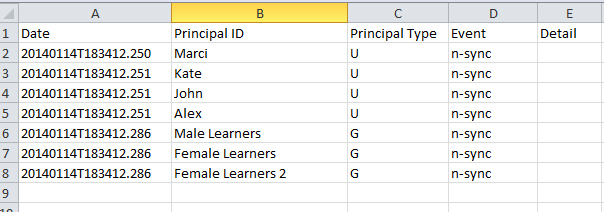
This time, you see the Event column shows ‘n-sync’ which literally means that the data is in-sync with the LDAP system and nothing was done to those records in Adobe Connect.
Now, let’s say I remove a user (Kate) from the directory completely. Then run the sync again. You will see in the logs the following (taking into consideration she is no longer in the directory):
From the new sync logs you can see that because I deleted Kate, 3 new actions needed to take place. The first you see are the two ‘update-members’ Events to both groups Kate belonged to. They both ‘removed’ Kate from the specific group (Female Learners and Female Learners 2). The other action was the actual ‘delete’ of the user Kate. Now, as you can see below, Kate is no longer in the Users and Groups in Adobe Connect.
Quickly looking at say the Female Learners group again, you can see Kate is gone from that group as well as she is obviously deleted.
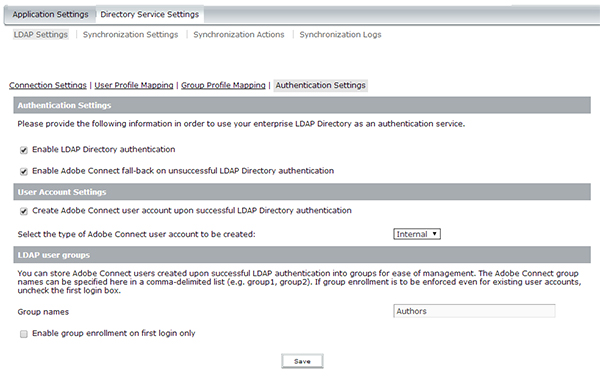
Lastly, here is a quick look at the Authentication Settings area. This is where you tell Adobe Connect how you plan on authenticating users. Since Adobe Connect doesn’t store passwords for LDAP users, you need to either configure Adobe to use it’s native LDAP authentication module to do a real-time authentication directly to the LDAP server when a user logs in on the Adobe Connect login page, OR tell Adobe not to do this, in anticipation of setting up a Single Sign On (SSO) solution via some other method (NTLM, HTTP Header Authentication, etc.).
If you do want Adobe to authenticate directly against the LDAP server (common scenario), you would make sure you check the box entitled ‘Enable LDAP Directory Authentication‘.
If you also want to be able to have both internal and external users log into Adobe Connect (internal users are users created IN Adobe Connect by an Administrator, external users are LDAP synched users), you need to check the second box which is ‘Enable Adobe Connect fall-back on unsuccessful LDAP Directory Authentication‘.
If you also want LDAP users who may have NOT been brought into the Adobe Connect system via a scheduled or manual sync yet, but the DO exist in the configured branches above, to be automatically created if they are successfully authenticated, you select the ‘Create Adobe Connect user account upon successful LDAP Directory authentication‘ option. This will cause the Adobe Connect system to take the login and password values from the user, check the LDAP server to verify that the user exists in the right place(s) you’ve specified in LDAP, and then if the user’s account does NOT exist yet, Adobe Connect will create their account on the fly, and let them right into their account. It will look to the user as if they were already created or had been synched before. This is handy if you have a scheduled synch say once a week, but new users come into the organization and need to access Connect before they are scheduled to be created via the sync.
The last common area in the Authentication settings is the ability to enroll these users into Adobe Connect Admin or System groups. Say you want to make everyone who authenticates to be added to an Adobe Connect system or admin group (like Authors, Meeting Hosts, Training Managers, or even a custom group like ‘AD Users’ that you’ve created), you can do so by adding a comma separated list of groups in the field entitled: ‘Group Names’ (as seen below).
Scenarios with the above options selected:
Example 1: User: Kim Fitzgerald is a user who has NOT been added to Adobe Connect yet via a synchronization, but has been added into the ‘Women’ OU in the LDAP directory (so if the sync were to execute now, she WOULD be found and brought into Adobe, but she is trying to access the system now, ahead of her being synched).
Kim hits the Adobe Connect login page and enters her username and password (LDAP user/pass). Adobe Connect will immediately check her credentials against the LDAP directory. She IS found in LDAP. Adobe Connect then checks it’s own database to see if the user has a profile that matches in Adobe. It does NOT find the profile. It will the create her profile for her automatically and let her immediately into her profile in Adobe Connect.
The logging looks like this (where the user: Kim, is found in LDAP, ALSO found in Adobe, and let into her profile):
[01-28 13:01:44,250] http-80-13 (INFO) [breezbreezipv9xwi2vgz82n7r:fe80:0:0:0:9066:51ea:28a4:281a] POST http://adobead-2bitqrp/system/login/ok?next=/&domain=http://adobead-2bitqrp&feature=1484=Login&login=Kim&set-lang=en&password=xxxxxxxxxx
[01-28 13:01:44,252] http-80-13 (INFO) 1ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:01:44,252] http-80-13 (INFO) 0ms spid:66 com.adobe.connect.dal.CoreDAL.hasActiveSession(“breezbreezipv9xwi2vgz82n7r”)
[01-28 13:01:44,255] http-80-13 (INFO) 2ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:01:44,257] http-80-13 (INFO) 2ms spid:57 com.adobe.connect.dal.CoreDAL.getUserSession(“adobead-2bitqrp”,”adobead-2bitqrp%”,”breezbreezipv9xwi2vgz82n7r”)
[01-28 13:01:44,259] http-80-13 (INFO) 2ms spid:57 com.adobe.connect.dal.CoreDAL.extendSessionExpirationDate(“10026807”)
[01-28 13:01:44,259] http-80-13 (INFO) 0ms spid:57 fetch com.macromedia.breeze.model.Config(“main”)
[01-28 13:01:44,260] http-80-13 (INFO) 0ms spid:57 fetch com.macromedia.breeze.model.Config(“directory”)
[01-28 13:01:44,260] http-80-13 (INFO) LDAPConfigReader: LDAP authentication is enabled with following settings:
[01-28 13:01:44,260] http-80-13 (INFO) LDAPConfigReader: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings:
AdminUsername: cn=Directory Manager
AdminPassword: (hidden)
AuthType: none
Group Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=groupOfNames)
isSearchRecursive: true
GroupMembershipMapping: member
GroupNameMapping: cn
QueryTimeout: 300
Query Page Size: 6
Url: ldap://ADOBEAD-2BITQRP:389
User Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 1: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Teachers,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 2: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Women,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 3: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Men,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
UserFirstnameMapping: givenName
UserLastnameMapping: sn
UserLoginMapping: uid
UserInfoMappings: {}
UserSyncMappings: {first-name=givenName, email=mail, login=uid, last-name=sn}
DirectoryMappings: {authentication-enabled=true, fallback-enabled=true, user-account-type=internal, create-user-account=true, user-groups-on-first-login-only=false, user-groups-enrollment=Authors}
[01-28 13:01:44,260] http-80-13 (INFO) LDAPConfigReader: Initial groups [Authors]
[01-28 13:01:44,260] http-80-13 (INFO) LDAPLoginManager: 1ms login configuration read
[01-28 13:01:44,260] http-80-13 (INFO) LDAPLoginManager: LDAP Action: login
[01-28 13:01:44,260] http-80-13 (INFO) LDAPLoginManager: External-auth ‘use’ directive ignored in favor of supplied login
[01-28 13:01:44,260] http-80-13 (INFO) LDAPLoginManager: Trying to login in Kim/********
[01-28 13:01:44,260] http-80-13 (INFO) LDAPAuthenticator: Attempting authentication on LDAP server default
[01-28 13:01:44,262] http-80-13 (INFO) LDAPUtil: Search for user at base DN [ou=Learners,dc=example,dc=com]
[01-28 13:01:44,262] http-80-13 (INFO) (&(uid=Kim)(objectClass=inetOrgPerson)) <== uid=Kim+(objectClass=inetOrgPerson)
[01-28 13:01:44,262] http-80-13 (INFO) LDAPUtil: with filter: ‘(&(uid=Kim)(objectClass=inetOrgPerson))’
[01-28 13:01:44,263] http-80-13 (INFO) LDAPUtil: Search for user at base DN [ou=Women,dc=example,dc=com]
[01-28 13:01:44,263] http-80-13 (INFO) (&(uid=Kim)(objectClass=inetOrgPerson)) <== uid=Kim+(objectClass=inetOrgPerson)
[01-28 13:01:44,263] http-80-13 (INFO) LDAPUtil: with filter: ‘(&(uid=Kim)(objectClass=inetOrgPerson))’
[01-28 13:01:44,265] http-80-13 (INFO) LDAPUtil: Match found: cn=Kim Fitzgerald,ou=Women,dc=example,dc=com
[01-28 13:01:44,266] http-80-13 (INFO) LDAPAuthenticator: AUTH SUCCESS: last, first / email = Fitzgerald, Kim / kim@mycompany.com
[01-28 13:01:44,266] http-80-13 (INFO) LDAPLoginManager: Login: { firstName: Kim, lastName: Fitzgerald, email: kim@mycompany.com, login: Kim, successfulLogin: true, custom: (), initialGroups: (Authors), userType: user, enroll once: false, fallBack: true
[01-28 13:01:44,266] http-80-13 (INFO) LDAPLoginManager: Trying to find user in DB…
[01-28 13:01:44,267] http-80-13 (INFO) 0ms spid:57 com.macromedia.airspeed.db.SQLServerUtilityQueries.setIsolationLevel(Enable Isolation)
[01-28 13:01:44,268] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.LDAPDAL.getUsersByLogin(“Kim”)
[01-28 13:01:44,269] http-80-13 (INFO) LDAPLoginManager: User not found in DB.
[01-28 13:01:44,269] http-80-13 (INFO) LDAPLoginManager: Create new user (Kim, Fitzgerald)
[01-28 13:01:44,269] http-80-13 (INFO) LDAP INVOKE action=custom-fields, params={filter-is-required=[true]}
[01-28 13:01:44,270] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.AccountDAL.getAccountFields(“7”,1)
[01-28 13:01:44,270] http-80-13 (INFO) 0ms spid:57 insert com.macromedia.breeze.model.Acl(“26808″,”7”)
[01-28 13:01:44,271] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808”)
[01-28 13:01:44,272] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808”)
[01-28 13:01:44,272] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808″,”26808”)
[01-28 13:01:44,273] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808″,”7”)
[01-28 13:01:44,274] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808″,”26808”)
[01-28 13:01:44,274] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.setParent(“26808″,”7”)
[01-28 13:01:44,275] http-80-13 (INFO) 1ms spid:57 fetch com.macromedia.breeze.model.AclField(“7″,”93”)
[01-28 13:01:44,275] http-80-13 (INFO) 0ms spid:57 fetch com.macromedia.breeze.model.User(“26808”)
[01-28 13:01:44,276] http-80-13 (INFO) 1ms spid:57 fetch com.macromedia.breeze.model.AclField(“7″,”93″)
[01-28 13:01:44,277] http-80-13 (INFO) 1ms spid:57 update com.macromedia.breeze.model.Principal(0,0,”Kim”,”7″,”Kim Fitzgerald”,”Kim”,”26808″)
[01-28 13:01:44,277] http-80-13 (INFO) 0ms spid:57 insert com.macromedia.breeze.model.Principal(0,0,”Kim”,”7″,”Kim Fitzgerald”,”Kim”,”26808″)
[01-28 13:01:44,278] http-80-13 (INFO) 1ms spid:57 update com.macromedia.breeze.model.Principal(“kim@mycompany.com”,”26808″,1)
[01-28 13:01:44,278] http-80-13 (INFO) 0ms spid:57 insert com.macromedia.breeze.model.Principal(“kim@mycompany.com”,”26808″,1)
[01-28 13:01:44,279] http-80-13 (INFO) 0ms spid:57 update com.macromedia.breeze.model.Principal(“Kim”,”26808″,2)
[01-28 13:01:44,279] http-80-13 (INFO) 0ms spid:57 insert com.macromedia.breeze.model.Principal(“Kim”,”26808″,2)
[01-28 13:01:44,280] http-80-13 (INFO) 0ms spid:57 update com.macromedia.breeze.model.Principal(“Fitzgerald”,”26808″,3)
[01-28 13:01:44,281] http-80-13 (INFO) 1ms spid:57 insert com.macromedia.breeze.model.Principal(“Fitzgerald”,”26808″,3)
[01-28 13:01:44,281] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“26808″,”26808″,”26808,”,0)
[01-28 13:01:44,282] http-80-13 (INFO) 0ms spid:57 com.macromedia.airspeed.db.DBConnection.update(“26808”)
[01-28 13:01:44,283] http-80-13 (INFO) 1ms spid:57 insert com.macromedia.breeze.model.User(“26808”)
[01-28 13:01:44,284] http-80-13 (INFO) 1ms spid:57 fetch com.macromedia.breeze.model.Preferences(“7”)
[01-28 13:01:44,284] http-80-13 (INFO) 0ms spid:57 update com.macromedia.breeze.model.Preferences(“26808″,”1″,”20”)
[01-28 13:01:44,285] http-80-13 (INFO) 1ms spid:57 insert com.macromedia.breeze.model.Preferences(“26808″,”1″,”20”)
[01-28 13:01:44,286] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.PrincipalDAL.getGroupByType(“7”,everyone)
[01-28 13:01:44,286] http-80-13 (INFO) 0ms spid:57 com.macromedia.airspeed.db.DBConnection.update(“11019″,”26808”)
[01-28 13:01:44,288] http-80-13 (INFO) 2ms spid:57 insert com.macromedia.breeze.model.GroupMember(“11019″,”26808”)
[01-28 13:01:44,288] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“11019″,”26808″,”11019,”,1)
[01-28 13:01:44,289] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“26808″,”11019,”,”11019″)
[01-28 13:01:44,290] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“26808″,”11019,%”,”26808″)
[01-28 13:01:44,290] http-80-13 (INFO) 0ms spid:57 update com.macromedia.breeze.model.AclEntry(“26808″,”17″,”26808”)
[01-28 13:01:44,291] http-80-13 (INFO) 1ms spid:57 insert com.macromedia.breeze.model.AclEntry(“26808″,”17″,”26808”)
[01-28 13:01:44,291] http-80-13 (INFO) LDAPLoginManager: New user created (26808)
[01-28 13:01:44,291] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.LDAPDAL.getPrimaryGroupsByAccount(“7”)
[01-28 13:01:44,292] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.PrincipalDAL.getPrincipalGroups(“26808”)
[01-28 13:01:44,292] http-80-13 (INFO) found primary group [11014]
[01-28 13:01:44,293] http-80-13 (INFO) 1ms spid:57 com.macromedia.airspeed.db.DBConnection.update(“11014″,”26808”)
[01-28 13:01:44,293] http-80-13 (INFO) 0ms spid:57 insert com.macromedia.breeze.model.GroupMember(“11014″,”26808”)
[01-28 13:01:44,294] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“11014″,”26808″,”11014,”,1)
[01-28 13:01:44,295] http-80-13 (INFO) 1ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“26808″,”11014,”,”11014″)
[01-28 13:01:44,295] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.CoreDAL.addGroupMembership(“26808″,”11014,%”,”26808″)
[01-28 13:01:44,295] http-80-13 (INFO) group type [authors]
[01-28 13:01:44,296] http-80-13 (INFO) 1ms spid:57 fetch com.macromedia.breeze.model.Principal(“26808”)
[01-28 13:01:44,297] http-80-13 (INFO) 1ms spid:57 fetch com.macromedia.breeze.model.Tree(“7”,3)
[01-28 13:01:44,297] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.PrincipalDAL.getUserShortcut(“26808″,”11001”)
[01-28 13:01:44,298] http-80-13 (INFO) 0ms spid:57 com.adobe.connect.dal.PrincipalDAL.getFolderByName(“Kim”,”11001″)
[01-28 13:01:44,298] http-80-13 (INFO) Successfully updated membership for group [Authors]
Example 2: User: Kim Fitzgerald is a user who is already in Adobe Connect. She was either added with a synch or created automatically via the ‘Create’ option as discussed above.
Kim hits the Adobe Connect login page and enters her username and password (LDAP user/pass). Adobe Connect will immediately check her credentials against the LDAP directory. She IS found in LDAP. Adobe Connect then checks it’s own database to see if the user has a profile that matches in Adobe. It DOES find the profile that matches. It then lets her immediately into her profile in Adobe Connect.
The logging looks like this (where the user: Kim, is found in LDAP, not found in Adobe, created in Adobe, and added to the applicable group – Authors):
[01-28 13:01:51,538] http-80-13 (INFO) [breezbreezipv9xwi2vgz82n7r:fe80:0:0:0:9066:51ea:28a4:281a] POST http://adobead-2bitqrp/system/login/ok?next=/&domain=http://adobead-2bitqrp&feature=1484=Login&login=Kim&set-lang=en&password=xxxxxxxxxx
[01-28 13:01:51,539] http-80-13 (INFO) 1ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:01:51,539] http-80-13 (INFO) 0ms spid:64 com.adobe.connect.dal.CoreDAL.hasActiveSession(“breezbreezipv9xwi2vgz82n7r”)
[01-28 13:01:51,540] http-80-13 (INFO) 0ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:01:51,543] http-80-13 (INFO) 2ms spid:78 com.adobe.connect.dal.CoreDAL.getUserSession(“adobead-2bitqrp”,”adobead-2bitqrp%”,”breezbreezipv9xwi2vgz82n7r”)
[01-28 13:01:51,544] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.CoreDAL.getWebSessionTimeoutByAccount(“26808”,web-session-timeout-minutes)
[01-28 13:01:51,544] http-80-13 (INFO) 0ms spid:78 com.adobe.connect.dal.CoreDAL.getWebSessionTimeoutByAccount(“7”,web-session-timeout-minutes)
[01-28 13:01:51,545] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.CoreDAL.extendSessionExpirationDate(“10026807”)
[01-28 13:01:51,546] http-80-13 (INFO) 0ms spid:78 fetch com.macromedia.breeze.model.Config(“main”)
[01-28 13:01:51,547] http-80-13 (INFO) 1ms spid:78 fetch com.macromedia.breeze.model.Config(“directory”)
[01-28 13:01:51,547] http-80-13 (INFO) LDAPConfigReader: LDAP authentication is enabled with following settings:
[01-28 13:01:51,547] http-80-13 (INFO) LDAPConfigReader: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings:
AdminUsername: cn=Directory Manager
AdminPassword: (hidden)
AuthType: none
Group Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=groupOfNames)
isSearchRecursive: true
GroupMembershipMapping: member
GroupNameMapping: cn
QueryTimeout: 300
Query Page Size: 6
Url: ldap://ADOBEAD-2BITQRP:389
User Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 1: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Teachers,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 2: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Women,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 3: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Men,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
UserFirstnameMapping: givenName
UserLastnameMapping: sn
UserLoginMapping: uid
UserInfoMappings: {}
UserSyncMappings: {first-name=givenName, email=mail, login=uid, last-name=sn}
DirectoryMappings: {authentication-enabled=true, fallback-enabled=true, user-account-type=internal, create-user-account=true, user-groups-on-first-login-only=false, user-groups-enrollment=Authors}
[01-28 13:01:51,547] http-80-13 (INFO) LDAPConfigReader: Initial groups [Authors]
[01-28 13:01:51,547] http-80-13 (INFO) LDAPLoginManager: 1ms login configuration read
[01-28 13:01:51,547] http-80-13 (INFO) LDAPLoginManager: LDAP Action: login
[01-28 13:01:51,547] http-80-13 (INFO) LDAPLoginManager: External-auth ‘use’ directive ignored in favor of supplied login
[01-28 13:01:51,548] http-80-13 (INFO) LDAPLoginManager: Trying to login in Kim/********
[01-28 13:01:51,548] http-80-13 (INFO) LDAPAuthenticator: Attempting authentication on LDAP server default
[01-28 13:01:51,549] http-80-13 (INFO) LDAPUtil: Search for user at base DN [ou=Learners,dc=example,dc=com]
[01-28 13:01:51,549] http-80-13 (INFO) (&(uid=Kim)(objectClass=inetOrgPerson)) <== uid=Kim+(objectClass=inetOrgPerson)
[01-28 13:01:51,549] http-80-13 (INFO) LDAPUtil: with filter: ‘(&(uid=Kim)(objectClass=inetOrgPerson))’
[01-28 13:01:51,550] http-80-13 (INFO) LDAPUtil: Search for user at base DN [ou=Women,dc=example,dc=com]
[01-28 13:01:51,550] http-80-13 (INFO) (&(uid=Kim)(objectClass=inetOrgPerson)) <== uid=Kim+(objectClass=inetOrgPerson)
[01-28 13:01:51,550] http-80-13 (INFO) LDAPUtil: with filter: ‘(&(uid=Kim)(objectClass=inetOrgPerson))’
[01-28 13:01:51,551] http-80-13 (INFO) LDAPUtil: Match found: cn=Kim Fitzgerald,ou=Women,dc=example,dc=com
[01-28 13:01:51,556] http-80-13 (INFO) LDAPAuthenticator: AUTH SUCCESS: last, first / email = Fitzgerald, Kim / kim@mycompany.com
[01-28 13:01:51,556] http-80-13 (INFO) LDAPLoginManager: Login: { firstName: Kim, lastName: Fitzgerald, email: kim@mycompany.com, login: Kim, successfulLogin: true, custom: (), initialGroups: (Authors), userType: user, enroll once: false, fallBack: true
[01-28 13:01:51,556] http-80-13 (INFO) LDAPLoginManager: Trying to find user in DB…
[01-28 13:01:51,557] http-80-13 (INFO) 1ms spid:78 com.macromedia.airspeed.db.SQLServerUtilityQueries.setIsolationLevel(Enable Isolation)
[01-28 13:01:51,558] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.LDAPDAL.getUsersByLogin(“Kim”)
[01-28 13:01:51,558] http-80-13 (INFO) LDAPLoginManager: user already exists (26808)
[01-28 13:01:51,558] http-80-13 (INFO) LDAPLoginManager: Re-applying group membership for user (26808)
[01-28 13:01:51,559] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.LDAPDAL.getPrimaryGroupsByAccount(“7”)
[01-28 13:01:51,559] http-80-13 (INFO) 0ms spid:78 com.adobe.connect.dal.PrincipalDAL.getPrincipalGroups(“26808”)
[01-28 13:01:51,560] http-80-13 (INFO) User already belongs to group [Authors]
[01-28 13:01:51,560] http-80-13 (INFO) 0ms spid:78 com.macromedia.airspeed.db.SQLServerUtilityQueries.setIsolationLevel(Disable Isolation)
[01-28 13:01:51,561] http-80-13 (INFO) 0ms spid:78 fetch com.macromedia.breeze.model.Principal(“26808”)
[01-28 13:01:51,562] http-80-13 (INFO) 1ms spid:78 fetch com.macromedia.breeze.model.User(“26808”)
[01-28 13:01:51,562] http-80-13 (INFO) 0ms spid:78 fetch com.macromedia.breeze.model.Account(“7”)
[01-28 13:01:51,563] http-80-13 (INFO) 0ms spid:78 update com.macromedia.breeze.model.Session(“10026807″,”26808”)
[01-28 13:01:51,564] http-80-13 (INFO) 0ms spid:78 com.adobe.connect.dal.CoreDAL.getUserSession(“adobead-2bitqrp”,”adobead-2bitqrp%”,”breezbreezipv9xwi2vgz82n7r”)
[01-28 13:01:51,565] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.CoreDAL.getWebSessionTimeoutByAccount(“26808”,web-session-timeout-minutes)
[01-28 13:01:51,565] http-80-13 (INFO) 0ms spid:78 com.adobe.connect.dal.CoreDAL.getWebSessionTimeoutByAccount(“7”,web-session-timeout-minutes)
[01-28 13:01:51,566] http-80-13 (INFO) 1ms spid:78 com.adobe.connect.dal.CoreDAL.extendSessionExpirationDate(“10026807”)
[01-28 13:01:51,566] http-80-13 (INFO) LDAPLoginManager: 20ms login executed
Example 3: User: Jim Johnson is an INTERNAL user (so not LDAP, but rather and Adobe Connect user only). He hits the login page for Adobe Connect and puts in his username and password. Adobe Connect STILL checks against LDAP first (this is just the way it works). Adobe will NOT find the user in LDAP of course. So as a ‘fall back’ , Adobe Connect still checks it’s own database and DOES find the user. It lets that user right into the profile if the user/pass combo are successfully authenticated.
The logging looks like this (where the user: Jim, is NOT found in LDAP, found in Adobe (so INTERNAL user), and let into his profile:
[01-28 13:10:15,242] http-80-4 (INFO) [breezbreezg2n745xt6sscfsk4:fe80:0:0:0:9066:51ea:28a4:281a] POST http://adobead-2bitqrp/system/login/ok?next=/&domain=http://adobead-2bitqrp&feature=1484=Login&login=Jim&set-lang=en&password=xxxxxxxxxx
[01-28 13:10:15,243] http-80-4 (INFO) 1ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:10:15,243] http-80-4 (INFO) 0ms spid:61 com.adobe.connect.dal.CoreDAL.hasActiveSession(“breezbreezg2n745xt6sscfsk4”)
[01-28 13:10:15,246] http-80-4 (INFO) 0ms NEW com.adobe.connect.dal.CoreDAL.hasActiveSession
[01-28 13:10:15,248] http-80-4 (INFO) 1ms spid:55 com.adobe.connect.dal.CoreDAL.getUserSession(“adobead-2bitqrp”,”adobead-2bitqrp%”,”breezbreezg2n745xt6sscfsk4″)
[01-28 13:10:15,249] http-80-4 (INFO) 1ms spid:55 com.adobe.connect.dal.CoreDAL.extendSessionExpirationDate(“10026809”)
[01-28 13:10:15,251] http-80-4 (INFO) 1ms spid:55 fetch com.macromedia.breeze.model.Config(“main”)
[01-28 13:10:15,252] http-80-4 (INFO) 1ms spid:55 fetch com.macromedia.breeze.model.Config(“directory”)
[01-28 13:10:15,252] http-80-4 (INFO) LDAPConfigReader: LDAP authentication is enabled with following settings:
[01-28 13:10:15,252] http-80-4 (INFO) LDAPConfigReader: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings:
AdminUsername: cn=Directory Manager
AdminPassword: (hidden)
AuthType: none
Group Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=groupOfNames)
isSearchRecursive: true
GroupMembershipMapping: member
GroupNameMapping: cn
QueryTimeout: 300
Query Page Size: 6
Url: ldap://ADOBEAD-2BITQRP:389
User Branch 0: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Learners,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 1: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Teachers,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 2: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Women,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
User Branch 3: com.macromedia.breeze.sync.drivers.ldap.LDAPSettings$LDAPBranchSettings:
DN: ou=Men,dc=example,dc=com
Filter: (objectClass=inetOrgPerson)
isSearchRecursive: true
UserFirstnameMapping: givenName
UserLastnameMapping: sn
UserLoginMapping: uid
UserInfoMappings: {}
UserSyncMappings: {first-name=givenName, email=mail, login=uid, last-name=sn}
DirectoryMappings: {authentication-enabled=true, fallback-enabled=true, user-account-type=internal, create-user-account=true, user-groups-on-first-login-only=false, user-groups-enrollment=Authors}
[01-28 13:10:15,252] http-80-4 (INFO) LDAPConfigReader: Initial groups [Authors]
[01-28 13:10:15,252] http-80-4 (INFO) LDAPLoginManager: 3ms login configuration read
[01-28 13:10:15,252] http-80-4 (INFO) LDAPLoginManager: LDAP Action: login
[01-28 13:10:15,252] http-80-4 (INFO) LDAPLoginManager: External-auth ‘use’ directive ignored in favor of supplied login
[01-28 13:10:15,252] http-80-4 (INFO) LDAPLoginManager: Trying to login in Jim/********
[01-28 13:10:15,252] http-80-4 (INFO) LDAPAuthenticator: Attempting authentication on LDAP server default
[01-28 13:10:15,254] http-80-4 (INFO) LDAPUtil: Search for user at base DN [ou=Learners,dc=example,dc=com]
[01-28 13:10:15,254] http-80-4 (INFO) (&(uid=Jim)(objectClass=inetOrgPerson)) <== uid=Jim+(objectClass=inetOrgPerson)
[01-28 13:10:15,254] http-80-4 (INFO) LDAPUtil: with filter: ‘(&(uid=Jim)(objectClass=inetOrgPerson))’
[01-28 13:10:15,255] http-80-4 (INFO) LDAPUtil: Search for user at base DN [ou=Women,dc=example,dc=com]
[01-28 13:10:15,255] http-80-4 (INFO) (&(uid=Jim)(objectClass=inetOrgPerson)) <== uid=Jim+(objectClass=inetOrgPerson)
[01-28 13:10:15,255] http-80-4 (INFO) LDAPUtil: with filter: ‘(&(uid=Jim)(objectClass=inetOrgPerson))’
[01-28 13:10:15,256] http-80-4 (INFO) LDAPUtil: Search for user at base DN [ou=Men,dc=example,dc=com]
[01-28 13:10:15,256] http-80-4 (INFO) (&(uid=Jim)(objectClass=inetOrgPerson)) <== uid=Jim+(objectClass=inetOrgPerson)
[01-28 13:10:15,256] http-80-4 (INFO) LDAPUtil: with filter: ‘(&(uid=Jim)(objectClass=inetOrgPerson))’
[01-28 13:10:15,257] http-80-4 (INFO) LDAPUtil: Search for user at base DN [ou=Teachers,dc=example,dc=com]
[01-28 13:10:15,257] http-80-4 (INFO) (&(uid=Jim)(objectClass=inetOrgPerson)) <== uid=Jim+(objectClass=inetOrgPerson)
[01-28 13:10:15,257] http-80-4 (INFO) LDAPUtil: with filter: ‘(&(uid=Jim)(objectClass=inetOrgPerson))’
[01-28 13:10:15,258] http-80-4 (INFO) LDAPLoginManager: Login failure: Jim
[01-28 13:10:15,258] http-80-4 (INFO) LDAPLoginManager: Attempting fall back to Connect user DB…
[01-28 13:10:15,259] http-80-4 (INFO) 0ms spid:55 com.adobe.connect.dal.PrincipalDAL.getUsersByLogin(“Jim”)
[01-28 13:10:15,263] http-80-4 (INFO) 2ms spid:55 fetch com.macromedia.breeze.model.Principal(“11070”)
[01-28 13:10:15,264] http-80-4 (INFO) 1ms spid:55 fetch com.macromedia.breeze.model.User(“11070”)
[01-28 13:10:15,264] http-80-4 (INFO) 0ms spid:55 fetch com.macromedia.breeze.model.Account(“7”)
[01-28 13:10:15,273] http-80-4 (INFO) 8ms spid:55 update com.macromedia.breeze.model.Session(“10026809″,”11070”)
[01-28 13:10:15,274] http-80-4 (INFO) 1ms spid:55 com.adobe.connect.dal.CoreDAL.getUserSession(“adobead-2bitqrp”,”adobead-2bitqrp%”,”breezbreezg2n745xt6sscfsk4″)
Common Questions/Answers:
Question: If I delete a user in LDAP that has been in Adobe and has been either a Meeting Host, Author, Training Manager, or Event Manager, does their content, meeting, training, or event folders get deleted (along with all their content)?
Answer: No. The individual user folders do not get deleted and the content remains on the system. It can be moved by an Admin to either another user’s folder or the shared content/meeting/training/event areas.
Question: If I delete a user in LDAP that has taken trainings, attended meetings, events, etc. , will their training transcripts and attendance/interaction data still persist in the Adobe Connect reports for those items?
Answer: Yes. If you run reports on specific courses, curricula, meetings, seminars, events, etc. , those users will show up in the reports. You will just not be able to run an individual report on that user any longer in the Reporting wizard. But they will show up in any of the main reports for those items.